Image Source: Top five technology investment trends 2024 | Verdict
Research company Gartner has forecast that global cybersecurity spending is projected to grow by 14% in 2024.
This uptick in spending comes from the reality that cyber risks have become a major concern amongst both businesses and consumers as more and more of the world economy happens online.
The focus on companies spending more on cybersecurity and risk management is great for investors. However, where exactly companies will focus their capital is an important question investors should know before investing in the industry.
The truth, is that the cybersecurity industry is still in its infancy as new and better technology will continue to drive change within the sector.
To help our readers prepare for the coming surge in global spending, below we have outlined the 4 major trends that are influencing how companies are preparing to protect their data and systems. Additionally, we have also identified one company for each trend that is at the forefront of using this new tech right now.
Cybersecurity Investment Trend #1: Artificial Intelligence & Machine Learning
Image Source: Closed Door Security – Machine Learning and Artificial Intelligence in Cyber Security: Automating Defence | CDSec
One of the most significant trends in cybersecurity investment is the increasing reliance on artificial intelligence (AI) and machine learning (ML). As cyber threats become more sophisticated, the traditional, rule-based approaches to security are no longer sufficient.
This is where AI and ML come into play, offering adaptive, intelligent solutions that can keep pace with the evolving threats of today’s world.
At the core of AI and ML in cybersecurity is the ability to analyze massive datasets far beyond human capacity. These technologies sift through data generated from network traffic, user activities, and application logs, looking for patterns that might indicate malicious activities.
By employing sophisticated algorithms, AI systems can identify subtle anomalies that might slip past traditional security measures. This pattern recognition is pivotal in detecting advanced persistent threats (APTs) and zero-day exploits, which are often designed to evade standard detection methods.
One of the most significant advantages of AI and ML in cybersecurity is the capability for automated responses. Upon detecting a threat, AI-driven systems can initiate predefined security protocols, such as isolating affected systems, blocking suspicious IP addresses, or initiating countermeasures.
Further, ML algorithms continuously learn from new data, meaning the system becomes more capable at identifying and responding to threats over time. This adaptive learning ensures that cybersecurity measures evolve along with emerging threats.
Investment Opportunity: CrowdStrike’s Use of AI in Cybersecurity

Image Source: CrowdStrike Falcon Agent | Cosive
CrowdStrike, a leader in cloud-delivered endpoint security, serves as a prime example of the effective use of AI and ML in cybersecurity. Their Falcon platform (pictured above) leverages AI to automate threat detection and response.
It continuously analyzes data from billions of endpoints worldwide, using sophisticated algorithms to detect and prevent breaches. This AI-driven approach allows CrowdStrike to identify threats more quickly and accurately, significantly reducing the time from threat detection to response.
Cybersecurity Investment Trend #2: Securing the Cloud

Image Source: Cybersecurity in the Cloud Era | FEI
When looking at how to improve data security and identity access management, cloud security has emerged as a crucial area of focus.
The current shift to remote work and cloud-based infrastructure requires a new approach to security and risk management, one which is tailored to the unique challenges of the cloud environment.
More specifically, cloud technology has allowed companies to store critical data off site, which can be a significant cyber risk in terms of data breaches and unauthorized access. And while the transition to the cloud has been happening for some time, this is a trend that still has significant room to run, as companies continue to find new ways to leverage the cloud for business operations. Research firm Gartner has forecasted that cloud-based spending will grow by 20% in 2024, as firms continue to transition services online.
Investment Opportunity: Zscaler’s Cloud Security Solutions

Image Source: Zscaler | KDDI America
One company that has proven to be the vendor of choice for companies looking to secure their cloud from the possibility of a data breach is Zscaler.
Zscaler’s approach to cloud security revolves around its cloud-native architecture, which is designed to provide secure access to applications and data in the cloud, regardless of the user’s location or device. Their security services include advanced threat protection, data protection, and access control, all delivered through a secure internet gateway that ensures safe and fast connectivity to the cloud.
Zscaler’s approach to cloud security comes through its innovative cloud-native architecture and the Secure Access Service Edge (SASE) model, which seamlessly integrates network security with wide-area networking capabilities. Central to their strategy is the Zero Trust Network Access (ZTNA) principle, emphasizing strict identity verification for every user and device, thereby significantly reducing the chance of unauthorized access.
Their platform excels in advanced threat protection, offering strong defenses against malware, ransomware, and advanced persistent threats, complemented by data protection features like data loss prevention (DLP), cloud access security broker (CASB) functionalities, and encryption. This ensures all-around security of data both in transit and at rest.
Additionally, the platform offers enhanced visibility into network traffic and user activities, providing crucial insights for real-time threat detection and mitigation.
Cybersecurity Investment Trend #3: Quantum Computing

Image Source: What The Quantum Computing Cybersecurity Preparedness Act Means For National Security | Forbes
Quantum computing introduces transformative capabilities in cybersecurity, primarily through the development of quantum-resistant cryptographic algorithms and Quantum Key Distribution (QKD) systems.
Unlike classical computing, quantum computers operate on quantum bits (qubits), enabling them to perform complex calculations at speeds unattainable by traditional computers. This ability poses a threat to current cryptographic standards, as quantum computers could potentially decrypt widely-used encryption algorithms used today.
In response, companies are investing in post-quantum cryptography (PQC), which involves designing cryptographic algorithms that are secure against both quantum and classical computers. These algorithms typically rely on mathematical problems that remain hard for quantum computers, such as lattice-based, hash-based, or code-based problems.
Additionally, Quantum Key Distribution harnesses the principles of quantum mechanics, particularly the phenomenon of quantum entanglement and the no-cloning theorem, to create a theoretically unbreakable method of key exchange.
In QKD, any attempt to eavesdrop on the key exchange alters the quantum state of the particles involved, thereby revealing the presence of an interceptor (apologies for how technical this is, however explaining quantum computing in simple terms is easier said than done).
This ensures absolute security in the transmission of encryption keys, which is a critical aspect of secure communications.
Investment Opportunity: Arqit’s Quantum Encryption Technology
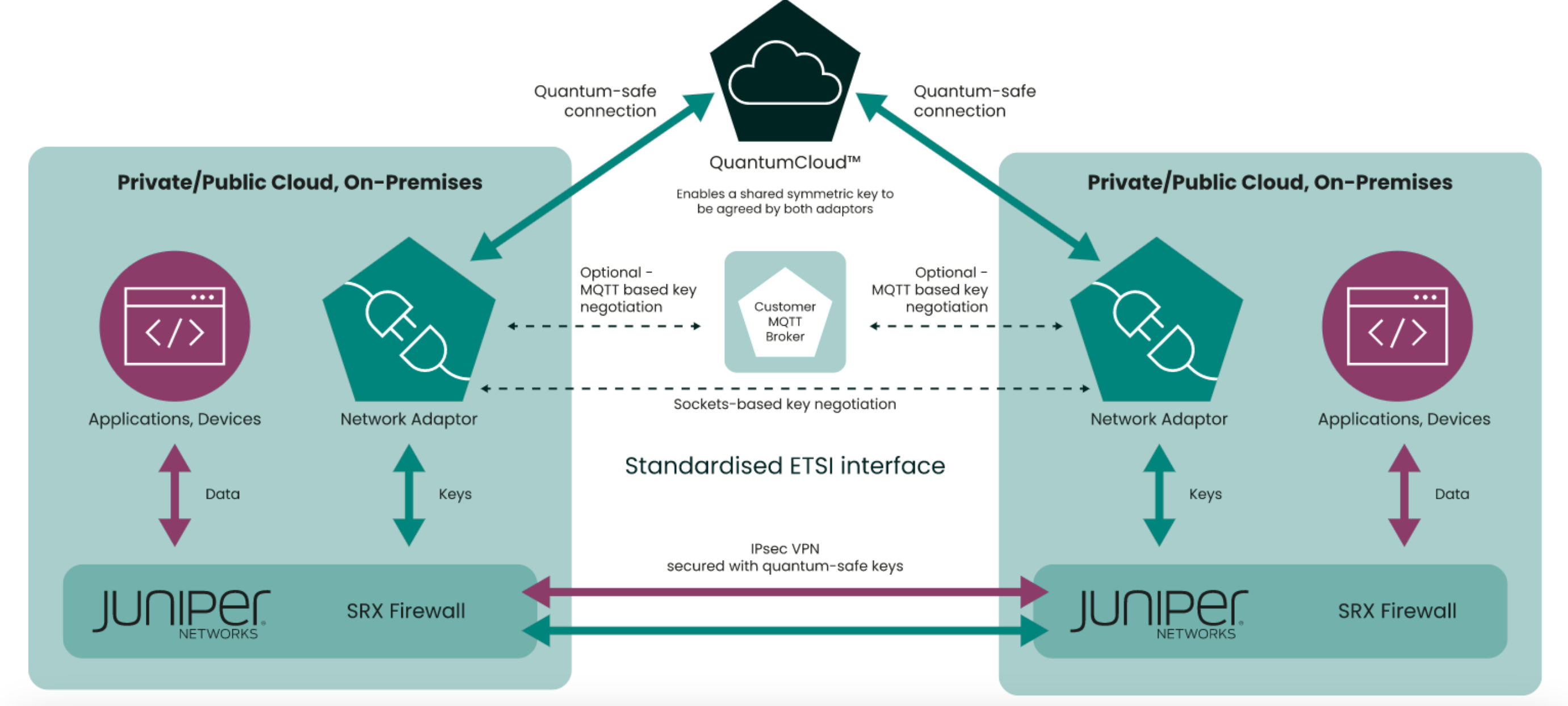
Arqit’s quantum encryption managed services represents a groundbreaking approach in cybersecurity, particularly in preparing for the quantum computing era.
Central to this technology is Quantum Key Distribution (QKD), which uses quantum mechanics principles to securely distribute cryptographic keys; meaning any interception attempt during transmission is detectable due to the alteration of the quantum state.
Complementing this, Arqit employs symmetric key encryption for efficient data encryption and decryption, ideal for high-speed data transfers. A key innovation in their system is the use of satellite-based key distribution, extending the reach and scalability of QKD beyond ground-based limitations.
Additionally, Arqit has developed a proprietary quantum-safe security protocol, designed to be resilient against potential decryption by quantum computers. This comprehensive approach not only prepares for future threats posed by quantum computing but also pioneers a new standard in secure communication, offering a robust solution for global-scale, quantum-safe encryption.
Cybersecurity Investment Trend #4: Blockchain Integration

Image Source: Blockchain Meets Cybersecurity | United States Cybersecurity Magazine
Blockchain technology, known primarily for its application in cryptocurrencies, is increasingly gaining attention in the field of cybersecurity. Its inherent characteristics of decentralization, transparency, and safety make it an attractive option for enhancing security across various digital platforms.
Blockchain technology offers unique advantages for cybersecurity. Its decentralized nature eliminates single points of failure, making systems more resilient to attacks. The transparency and security of blockchain ensure that any alterations to data are easily traceable and verifiable, enhancing data integrity. These features are particularly beneficial for securing critical infrastructure and IoT devices, where the integrity of data is critical.
Investment Opportunity: Xage Security’s Blockchain Solution
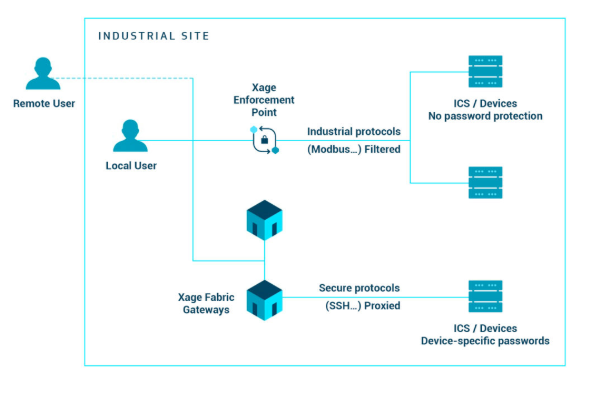
Image Source: New Blockchain Solution for IIoT Aims to Solve Scaling Problem | SecurityWeek
Xage Security leverages blockchain to create decentralized, tamper-proof security systems. Their solutions focus on securing industrial IoT and critical infrastructure, where traditional cybersecurity measures often fall short. By utilizing a blockchain-based platform, Xage creates a unified security fabric that ensures consistent enforcement of security policies across diverse devices and networks.
Xage’s implementation of blockchain in cybersecurity stands out for its ability to scale while maintaining high security and operational efficiency. Their security platform uses blockchain to create a distributed, redundant system where each node contributes to the overall security, making it highly resilient to attacks. Furthermore, Xage’s solution is designed to be flexible and interoperable, capable of integrating with existing infrastructure and various types of devices.
Wrap Up
It’s clear that the future of cybersecurity is poised for dynamic and transformative change. Risk management spending is locked in for significant growth as we enter 2024 and beyond, as companies realize the need to improve their ability to prevent cyber attacks from happening.
Within the industry, a few trends are defining where the cybersecurity market will go next. Specifically, AI, cloud security, quantum computing, and blockchain integration are proving to be the future of how companies will protect their digital infrastructures from malicious attacks.
Additionally, within these trends are a select few companies that are moving quickly to implement and perfect these technologies today.
The key takeaway here is that the future of cybersecurity is intrinsically linked to ongoing technological advancements.
And today, marks a special opportunity for investors to gain financially from these trends as cybersecurity defences become a focus across entire economies worldwide.
Disclosure/Disclaimer:
We are not brokers, investment, or financial advisers; you should not rely on the information herein as investment advice. If you are seeking personalized investment advice, please contact a qualified and registered broker, investment adviser, or financial adviser. You should not make any investment decisions based on our communications. Our stock profiles are intended to highlight certain companies for YOUR further investigation; they are NOT recommendations. The securities issued by the companies we profile should be considered high risk and, if you do invest, you may lose your entire investment. Please do your own research before investing, including reading the companies’ public filings, press releases, and risk disclosures. The company provided information in this profile, extracted from public filings, company websites, and other publicly available sources. We believe the sources and information are accurate and reliable but we cannot guarantee it. The commentary and opinions in this article are our own, so please do your own research.
Copyright © 2023 Edge Investments, All rights reserved.
